Microsoft have recently announced that the Azure Sentinel solution has been released for general availability. Since its launch as a preview in February this year, Microsoft have collected feedback from 12,000 customers and more than two petabytes of data analysis to examine.
What is Azure Sentinel?
Microsoft Azure Sentinel is a scalable, cloud-based security information event management (SIEM) solution that delivers additional security orchestration automated response (SOAR) capabilities. Using AI to analyse large volumes of data from users, applications, servers and devices on-premise or in any cloud, Azure Sentinel gives you a bird’s eye view over the enterprise – fast.
Some of the major challenges security teams face now are the increasing complexity of threats, the stress of too much noise and alert fatigue. According to Ann Johnson, Corporate Vice President of Microsoft’s Cybersecurity Solutions Group, early adopters saw a 90 percent reduction in alert fatigue, and the timeline of threat hunting drop from hours to seconds.
Rather than presenting an endless series of alerts, Azure Sentinel correlates multiple alerts that combined indicate a potential threat that should be investigated and resolved. These groups of alerts are called incidents. By streamlining this process, enterprise security teams can scale up their threat hunting, detection and response efforts without dramatically increasing their resources.
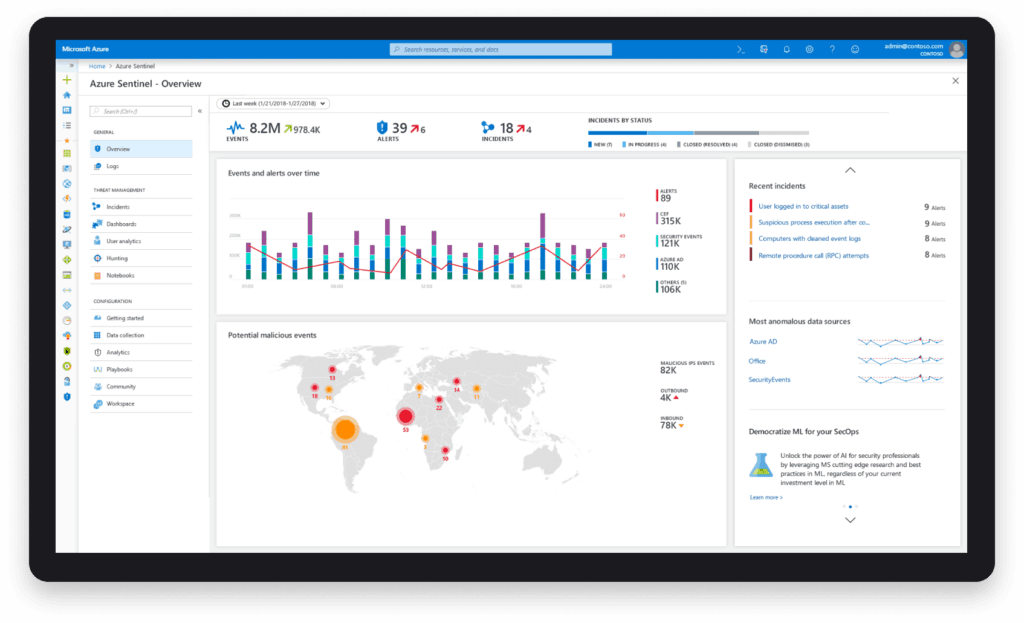
Organisations can now build their own correlation rules to combine alerts across different sources and perform remediation actions based on these incidents. Sources include Microsoft applications (Office 365, Azure Active Directory, Azure Active Directory Identity Protection etc) as well as third-party applications such as Palo Alto Networks firewalls or Symantec security solutions.
Security teams can now also write their own playbooks and automate responses to security incidents seen across their own environment. The response to an incident can either be a simple alerting and notification action or alternatively, trigger actions in multiple solutions to block an attack or compromise attempt.
For example, if unusual behaviour is exhibited by a user or device accessing Office 365 sources and it is detected through Azure Active Directory Identity Protection, an action can be triggered through Azure Sentinel Playbooks to block the user accessing other resources via a Palo Alto Networks firewall.
Interested in finding out more about Microsoft Azure Sentinel? Get in touch with our team.


![[M365 AI] Copilot & AI Agents: Tips You Must Know](https://www.threatscape.com/wp-content/uploads/2025/07/COPILOT-PODCAST-3.jpg)

![[M365 AI] Copilot & AI Agents: Tips You Must Know](https://www.threatscape.com/wp-content/uploads/2025/07/COPILOT-PODCAST-3-300x169.jpg)



