
Abnormal is the most precise human behaviour security engine for blocking all email attacks, including phishing, malware, ransomware, social engineering, executive impersonation, supply chain compromise, internal account compromise, spam, and graymail.
A Fundamentally Different Approach to Email Security
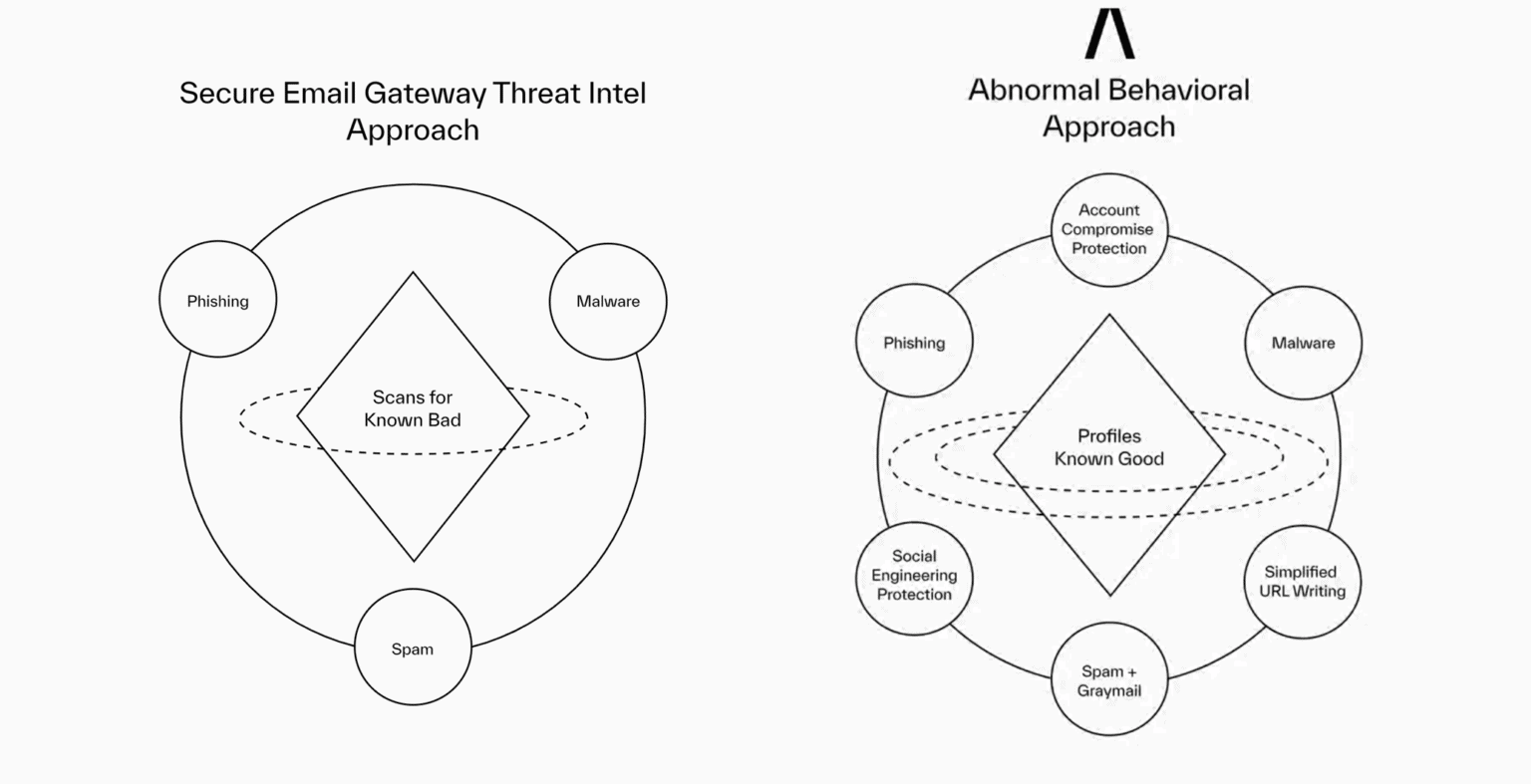
Secure email gateways and built-in Microsoft and Google security struggle to block email attacks that pass reputation checks, have no URLs or attachments, and appear to come from trusted sources.
Only Abnormal uses behavioural AI to profile known good behaviour and analyses over 45,000 signals to detect anomalies that deviate from these baselines, delivering maximum protection for global enterprises.
Why Choose Abnormal?
Abnormal profiles known good behaviour and analyses over 45,000 signals to detect anomalies that deviate from these baselines. Only Abnormal precisely blocks all socially-engineered and unwanted emails—both internal and external—and detects and remediates compromised accounts.
Abnormal integrates with multiple Microsoft 365 and Google Workspace tenants in minutes, with one click and no disruption to mail flow.
Simplify your email security stack by eliminating the redundant email gateway layer, and re-enabling and enhancing Microsoft’s cloud gateway capabilities. Unify your entire inbound email security defences, from email hygiene to zero-day advanced attacks.
Abnormal provides a native Microsoft email experience that puts an end to spam digests and portals. With deep integration into Microsoft and Google via APIs, Abnormal learns each end user’s preference as they move emails between inbox, spam, and promotional folders within their mailboxes.
Abnormal Security Solutions
Contact us for a no-obligation trial
Installation takes less than five minutes!
Resources
CISO Guide to Ransomware
In this white paper we examine the current ransomware landscape, increasingly common methods used by threat actors in ransomware attacks, and the business impact seen by victims of ransomware.
CISO Guide to Business Email Compromise
In this white paper, we explore the rising threat of Business Email Compromise, the types of BEC attacks seen today, and tactics for securing your organisation against email threat actors.
CISO Guide to Phishing
In this white paper we explain the varieties of phishing attacks being lodged against organisations and explore the route to improved protection.
The Role of AI in Email Security
In this white paper we explore where AI fits in alongside traditional email security solutions, along with how it is being leveraged by threat actors.
H2 2023 Email Threat Report
In this threat report, we outline recent changes to the email threat landscape, documenting the rise in attacks, and opportunities to modernise effective protection.
Total Economic Impact of Abnormal Security Report (Forrester)
In this impact report Forrester presents an assessment of the costs and benefits associated with deploying Abnormal Security within your organisation.
Q3-2021 Email Threat Report
There is little doubt that business email compromise and other advanced email threats are causing significant damage–both financial and reputational—to organizations worldwide.
Email Security Architectures From Exchange to Microsoft 365
With the early market adoption of on-premise mail servers like Microsoft Exchange, organizations also implemented security measures to protect against the wide array of email threats.
The Essential Guide to Cloud Email Security
As organisations have moved to cloud-based infrastructure and productivity platforms like Microsoft 365 and Google Workspace, they’ve seen key benefits including easier collaboration, greater agility, and lower costs and maintenance related to infrastructure.
CISO Guide to Vendor Email Compromise (VEC)
Vendor email compromise (VEC) is a significant security threat to enterprise organizations. This form of attack occurs when a threat actor gains control of a vendor email account and then uses it to steal money from known contacts.
©2021 Abnormal Security Corp. All rights reserved














