Please see below details of a further security threat related to Zoom video conferencing which we wanted to bring to your attention. We apologise for sending two alerts regarding Zoom within 24 hours, but felt it was warranted on this rare occasion since many clients have recently adopted Zoom as part of their remote working strategy during the Covid-19 crisis. We fear the methods described below to compromise calls could be widely exploited in the days ahead and that IT security personnel should now remind their colleagues to set a password for every Zoom call they might organise.
Also to be clear – we are not seeking to criticise Zoom; indeed we applaud how they have scaled up their infrastructure to cope with the staggering growth in their user base. Their daily meeting participants have grown from 10 million to 200 million in just three months, including 90,000 schools in 20 countries who now rely on their platform to reach students at home. Boris Johnson even held a cabinet meeting by Zoom last week. But while it was inevitable that this surge in popularity would focus increased attention on Zoom from security researchers, the number of issues uncovered do raise concerns.
Amongst other things, they were not up front about how they utilise user data including linking to Facebook and LinkedIn, and their claims to provide end to end encryption were false. We hope they will quickly remedy these issues, and welcome the announcement that they are to cease new feature development for 90 days to focus instead on bolstering their privacy and security.
Threat Advisory
This advisory details a recently discovered threat related to a widely adopted technology which may be applicable to your business, and contains our recommendations on how you can mitigate its effects.
Title: New hacking tool can discover and gate-crash Zoom meetings if organisers don’t set a meeting password
Date: April 2nd, 2020
Summary: Hacking tool exposes unprotected Zoom calls to eavesdropping or disruption
Details
Each Zoom video-conference call is assigned a Meeting ID of between 9 and 11 digits in length. Hackers merely need to guess random numbers to search for active or scheduled calls, and if they guess right they can disrupt or eavesdrop on the call if the organiser hasn’t used a password to protect it.
A new hacking tool called “zWarDial” automates and accelerates the process of guessing numbers and searching for insecure meetings.
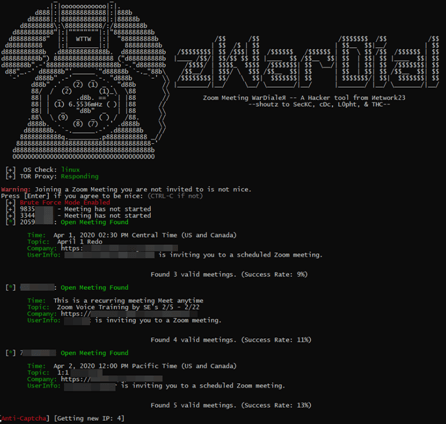
The ease of finding insecure calls makes it inevitable these techniques will be widely used in the days ahead for both mischief and corporate espionage.
Zoom tries to block automatic scans like this, but zWarDial circumvents their security by using the Tor network to operate from multiple IP addresses.
Zoom last year enabled passwords by default for new calls but organisers can opt out. Security researchers have found many calls remain unprotected, including some organised by major firms conducting sensitive business discussions.
Mitigation Steps
Further Reading
(on this and other Zoom security issues)
Krebs on Security: “War-Dialing tool exposes Zoom’s Password problems”
https://krebsonsecurity.com/2020/04/war-dialing-tool-exposes-zooms-password-problems/
Zoom disables feature which data-mined user’s LinkedIn profiles:
https://threatpost.com/zoom-removes-data-mining-linkedin-feature/154404/
Zoom meetings are NOT end-to-end encrypted despite their claims
https://theintercept.com/2020/03/31/zoom-meeting-encryption/
Zoom freezes feature development to fix security and privacy issues








